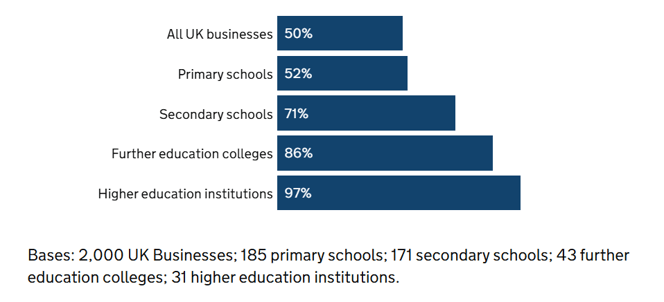
The results from the UK government’s Cyber security breaches survey 2024: education institutions annex has highlighted a vital need for schools to review their data security measures. The survey identified that 52% of primary and 71% of secondary schools identified a data breach in the last year.
Recommended guidance and top tips
To ensure that you are being pro-active in possible data breaches at your establishment, we suggest that you follow the below guidance and ensure all staff members are educated on the importance of following these steps to prevent possible attacks on your school.
1. Enhance staff and student awareness
- Regular training: Provide ongoing cybersecurity training for staff and age-appropriate lessons for students. Check out the UK’s National Cyber Security Centre (NCSC) for information on Cyber Security Training for School Staff, where staff can gain a certificate upon competition.
- Passwords: Prompt all staff to change their passwords regularly and always use strong passwords. Ensure staff never share passwords and do not use the same username and passwords to log in to multiple systems.
- Phishing simulations: Run simulated phishing campaigns to train staff on how to spot suspicious emails.
- Exit-staff process: Ensure you have a process for when staff leave your school, removing all access from relevant software and ensure their security details are not saved in an accessible place.
2. Implement strong access controls
- Two-factor authentication (2FA): Require 2FA for staff accessing sensitive systems or data. Coming soon to ReachMoreParents, information to follow in due course.
- Role-based access: Limit access to data and systems based on staff roles (e.g., admin vs. teaching staff). Restrict who has the permissions to create and remove accounts and ensure staff are not sharing accounts.
3. Keep systems and software updated
- Patch management: Ensure all operating systems, applications, and devices are updated promptly.
- Automatic updates: Enable automatic updates where possible, especially for antivirus and firewall systems.
4. Strengthen network security
- Firewalls and antivirus: Use enterprise-level firewalls and regularly updated antivirus software. Ensure antivirus and anti-malware software is installed on all devices, including servers, staff laptops, and student-access terminals. Keep definitions updated automatically and regularly scan for threats.
- Segregated networks: Separate guest/student Wi-Fi from the main school network. This helps contain threats—if a student device is compromised, it won’t affect systems that manage payroll, attendance, or safeguarding information. Use VLANs (Virtual Local Area Networks) to manage this effectively.
5. Regular risk assessments
- Cyber audits: Conduct regular audits to identify vulnerabilities. This includes reviewing user access rights, checking for unpatched systems, identifying outdated hardware or software, and ensuring security controls are working as intended. Use tools provided by the NCSC or a trusted IT partner.
- Penetration testing: Employ external experts to test your systems for weaknesses. This simulates real-world attacks and exposes vulnerabilities that might not be caught in routine audits. Ensure findings are documented and addressed promptly.
6. Backup and disaster recovery planning
- Regular backups: Automatically back up important data and store it securely ideally a secure offsite server and a cloud-based system that uses encryption.
- Incident response plan: Have a clear and tested plan for how to respond to different types of attacks. Ensure the plan includes roles and responsibilities, internal and external communication protocols, and contact details for relevant authorities such as the NCSC and local authority. Practice response drills to build staff confidence in handling emergencies.
7. Engage with national cybersecurity resources
